The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.
The hackers have been releasing data since 2016 when they auctioned off exploits stolen from the NSA-linked Equation Group. Last week, the group published the password on Medium for the alleged NSA files which they failed to auction off for one million Bitcoin (around $500 million) last year.
Now, the group has dumped a bunch of hacking tools targeting unpatched and older versions of Microsoft Windows and evidence that the Equation Group had gained access to servers and targeted the SWIFT banking system, specifically the SWIFT Service Bureau of the Middle East, EastNets.
UPDATE: Microsoft released a statement late Friday night confirming that the March Patch Tuesday included fixes to kill these zero day SMB exploits in all supported versions of Windows. So, if you're running Windows 7, 8, 8.1, or 10 and have installed all available updates via Windows Update as of last month, then your system is protected.
EastNets released an official statement stating that none of its services have been compromised:
The reports of an alleged hacker-compromised EastNets Service Bureau (ENSB) network is totally false and unfounded. The EastNets Network internal Security Unit has ran a complete check of its servers and found no hacker compromise or any vulnerabilities. The EastNets Service Bureau runs on a separate secure network that cannot be accessed over the public networks. The photos shown on twitter, claiming compromised information, is about pages that are outdated and obsolete, generated on a low-level internal server that is retired since 2013.
However, the dumped data reveals that the NSA was looking to have an eye into SWIFT and possibly the entire banking network. Matt Suiche, a French hacker and founder of MoonSols, believes that the leaks reveal a good way for an attacker to gain information on how "a SWIFT Service Bureau actually works and its internal infrastructure," which could compromise SWIFT's Service Bureaus down the line.
The Shadow Brokers dump is broken down into three categories: Oddjob, SWIFT, and Windows.
- Oddjob is a series of tools including logs, Excel spreadsheets, and PowerPoints of top secret documents, which reveals that the hacker group not only had access to exploits, but also to inside information.
- SWIFT data reveals the internal infrastructure map of the SWIFT network and also its scripts, tools, and many other leaks.
- The aptly named Windows collection contains a series of exploits targeting older versions of Windows, including what appeared to be a number of zero days targeting SMB (Windows protocol for file sharing over a network), specifically, though it has now been confirmed that they only affect outdated and unsupported versions of Windows ranging from Windows 2000/XP up through Windows Vista (though unpatched versions of Windows 7 may still be affected, so make sure you've installed all available updates on your system). The file also contains what Suiche says is data to "fuzzbunch the 'NSA-metasploit.'"
It has been said by Edward Snowden that the Shadow Brokers are possibly linked to Russia. Many others, such as the news agency Reuters, disagree and believe that the group is not a group but rather—another disgruntled NSA employee.
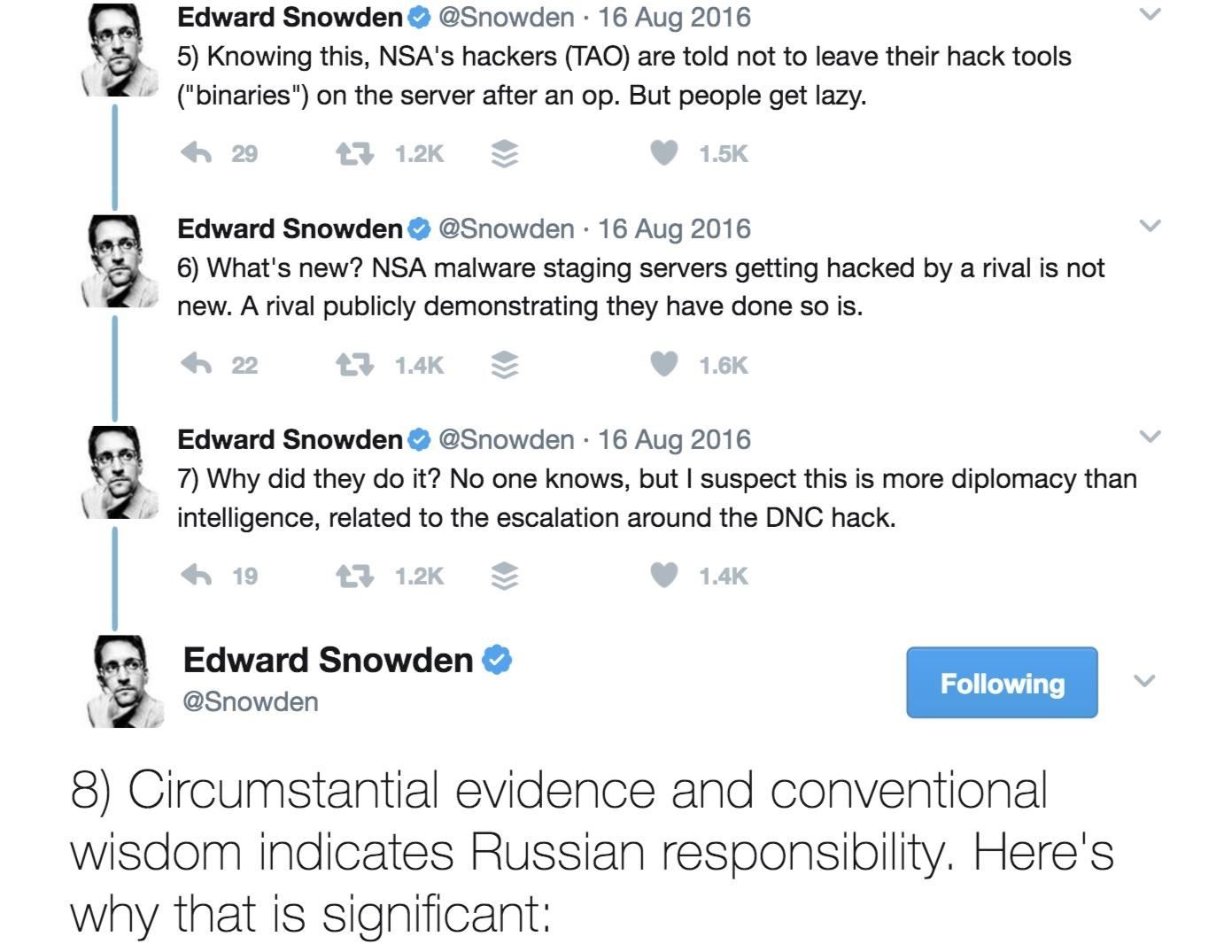
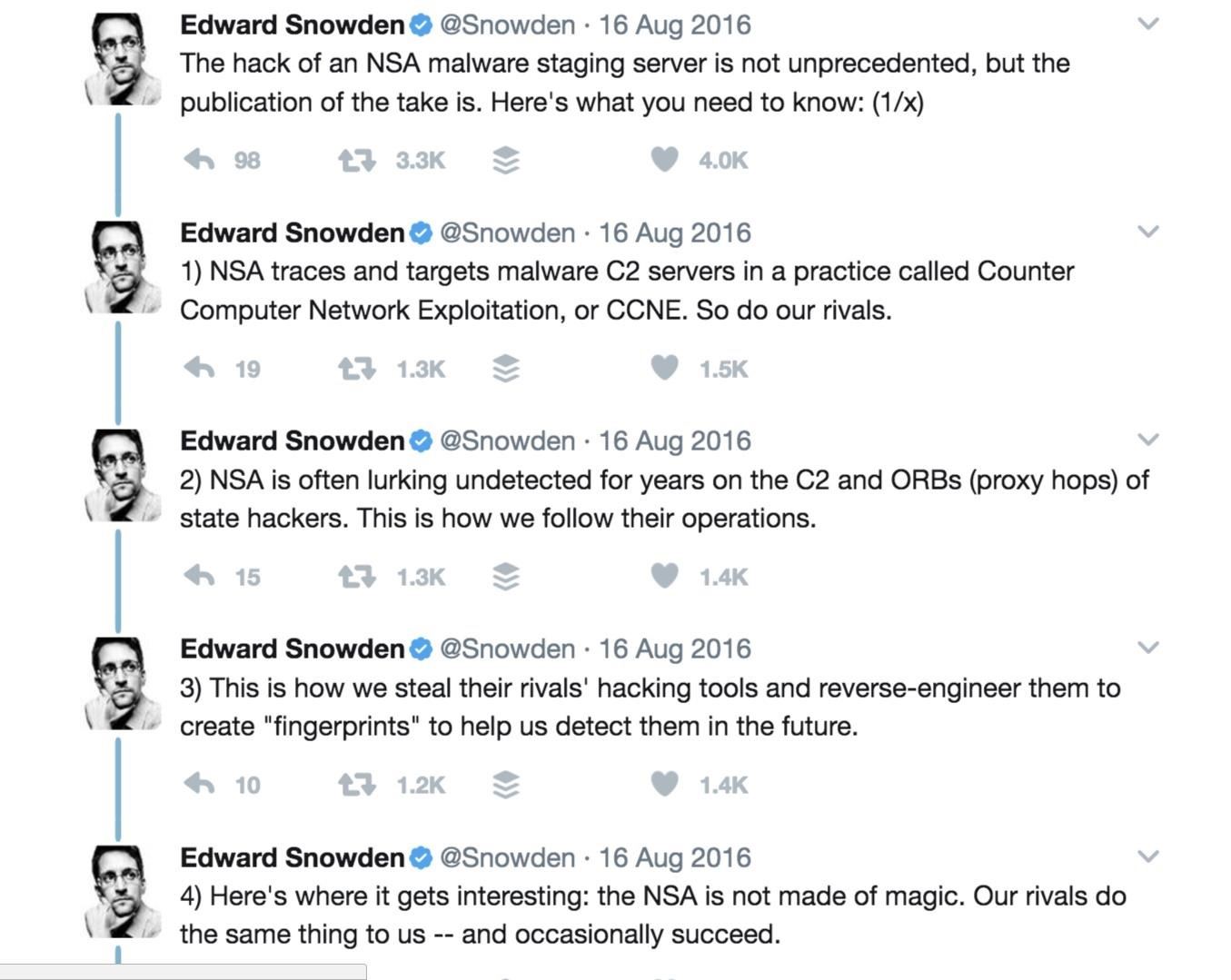
The New York Times even famously speculated that the Shadow Brokers' dump in 2016 was tied to the Democratic National Committee cyberattacks and the email hack of John Podesta, Hillary Clinton's presidential campaign chairman.
Whether the group is tied to Russia or not, they accommodated the remaining data leak with their very peculiar way of speaking in broken English:
Dear President Trump,
Respectfully, what the fuck are you doing? TheShadowBrokers voted for you. TheShadowBrokers supports you. TheShadowBrokers is losing faith in you. Mr. Trump helping theshadowbrokers, helping you. Is appearing you are abandoning "your base", "the movement", and the peoples who getting you elected.
You can check out one of the SMB exploits in action on Twitter, posted by Hacker Fantastic, where he shows us ETERNALBLUE, a zero day remote code execution, being used to compromise an unpatched Windows Server 2008 R2 host with Fuzzbunch, a framework similar to Metasploit, in less than 2 minutes:
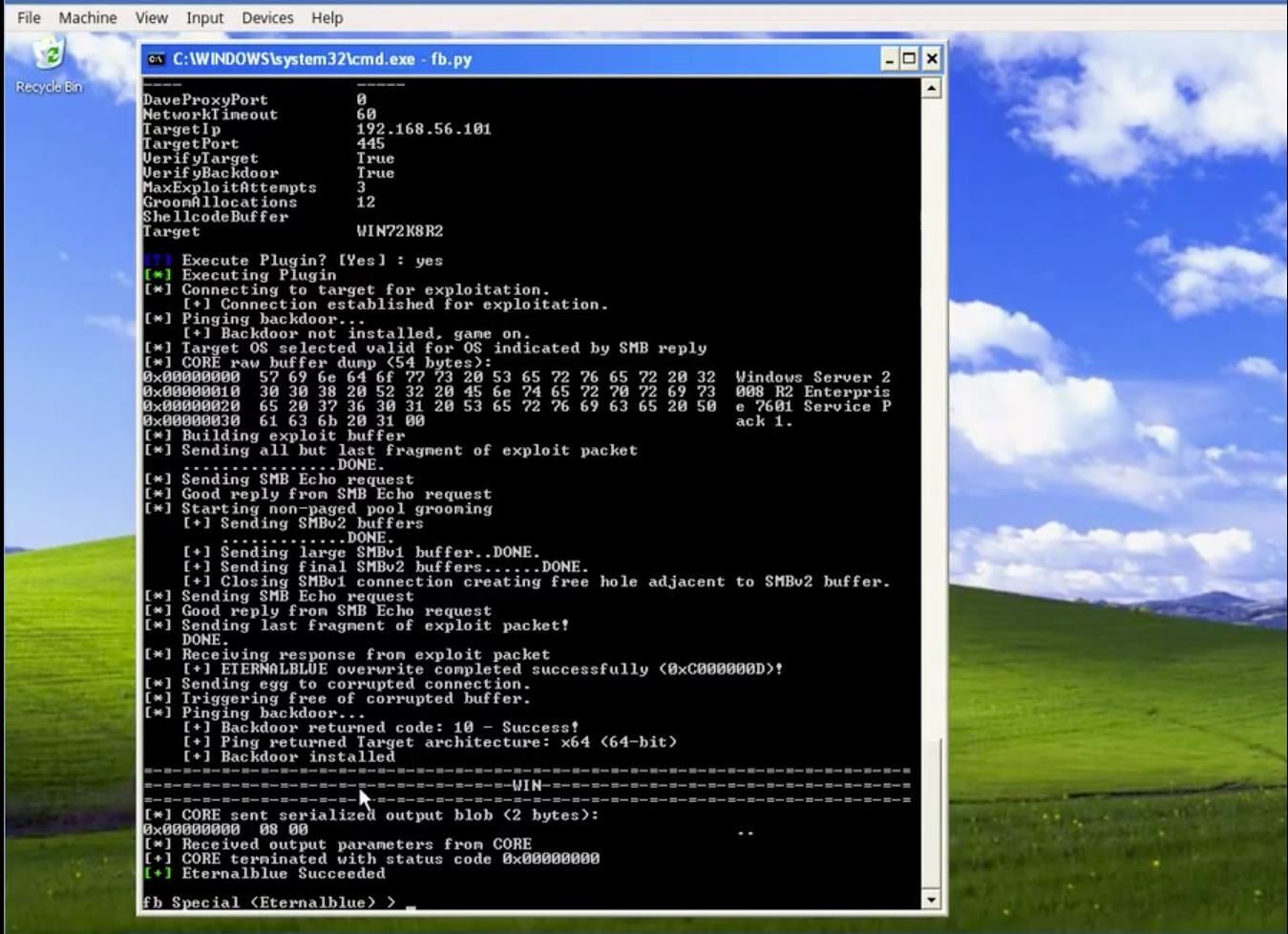
All the files from the current dump have been unzipped and are located on GitHub for you to look through. Researchers are already combing through the recent dump in a #shadowbrokers chatroom on the Freenode IRC channel while working through the data on a public collaboration pad. A user by the nickname <drwolf> suggests that if the Shadow Brokers had access to SWIFT data, then they had access to much more. The user also speculates that the next dump will have even more targets.
Some American's consider or maybe considering TheShadowBrokers traitors. We disagreeing. We view this as keeping our oath to protect and defend against enemies foreign and domestic. TheShadowBrokers wishes we could be doing more, but revolutions/civil wars taking money, time, and people. TheShadowBrokers has is having little of each as our auction was an apparent failure. Be considering this our form of protest.
The question many are asking now, and have been since 2016, is if the NSA knew their tools were stolen, and that these were going to be leaked, why didn't they warn Cisco, Microsoft, and others of these exploits so they could be closed before the leak? That would have been a surefire way to stop the hackers in their tracks. The question has yet to be answered and remains unknown.
Any guesses as to why the NSA chose not to warn Cisco and Microsoft? Find anything new and interesting in the leaks? Comment below with your thoughts as the Shadow Brokers leaks continue to be uncovered.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























Be the First to Comment
Share Your Thoughts